What is a Door?
Doors are one of the most vital components of someones security. These provide the first line of defense in our residential home and similar buildings, and provide a last line of defense in an apartment, hotel, and bedroom. Doors act as a symbol in our minds, of boundaries from the inner and the outer and may be the most potent symbol of this (1), possibly less than walls but that is a digression. We could spend this post discussing the psychic implications of doors and do a literature review of this. However, that is well beyond the scope of 1) my degree, and 2) this blog generally speaking. But we can discuss something else, how secure are doors? Are they really a suitable solution to ones security concerns? And if by default the answer is no, what can be done to fix this? The point of this post is to give a cursory overview of different methods people use to bypass doors and get into a secured area. Doors are the front, and in many cases, last line of defense between people and businesses and the outside world. As a result I have taken a very keen interest in starting to learn low tech solutions to getting through a door. I am omitting the electric solutions since that will tie into another project I am working on and I have really narrowly focused in on certain topics in regards to electronic door locks.
I think it goes without saying, but if you do want to practice any of these make sure you have permission. It is usually very illegal to do any of this willy nilly and people aren’t going to really believe, “I was just practicing I swear all these break in tools aren’t nefarious!”.
The Lock, The Latch, and the Fitting

The lock itself is probably the most looked at piece in terms of defeating a lock and has stolen a lot of glory. This is a dangerous thing I feel, as it really limits the defenders perception of the various flaws in the security of their doors. But I digress, here let’s talk about the various problems with the locking mechanism itself and ways it can be exploited and avoided entirely through direct manipulation. There is a whole lot more to exploiting locks than just cracking out your 11$ lock picking set your ordered on amazon and snapping the rake inside of the lock disabling it entirely.
Lock Picking

So let’s talk about the problems that lock picking can present. This is probably the most well known, if not the least likely to be used, method for bypassing most doors. Locks have followed the same basic construction for decades/centuries. One has a rotating cylinder/latch which has a series of pins, bars, rings, etc. blocking the motion of the locking mechanism. When a key is inserted it unblocks the cyclinder, or in more primitive locks moves the latch directly. Most locks are pin and tumbler locks (see the lock below), there are also disc detainer locks, wafer locks, among with a host of others that one can learn about. I am not a locksmith, or even a particularly great lock picker so this will be kept simple. If you want to learn about lock picking go to your regional Toool organization in order to get started well. The basic premise is the same across all of these (mostly), there is a central core that needs to be spun in order to engage a bolt/latch and disable the locking mechanism. We’ll look at the three mentioned types of locks and talk about bypassing them and the tools required.
Pin & Tumbler
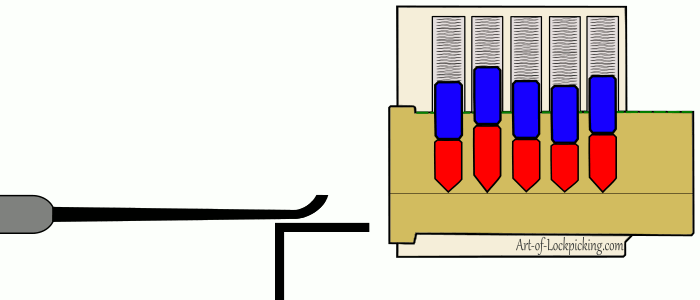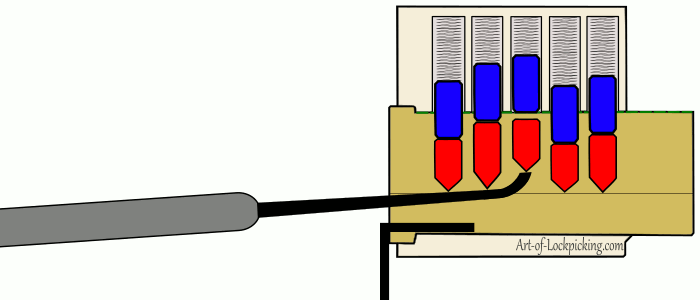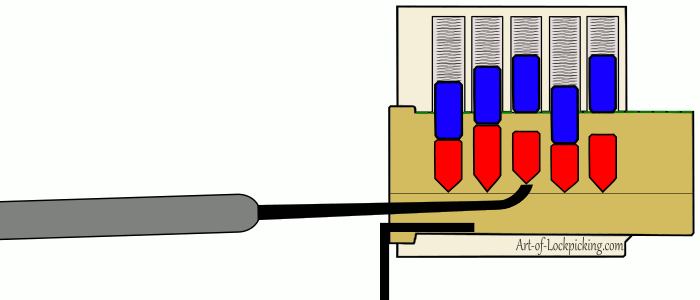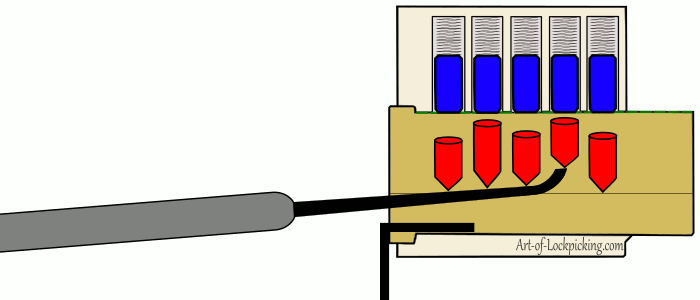
The most classic example of a lock if I could imagine one is the pin and tumbler. If you have seen television shows or movies of people picking locks (probably poorly), or played a game where you are picking locks the actions being pantomimed are those of pin and tumbler lock picking. The gif above gives a visual representation of the process one undergoes, but it is as follows: The picker inserts a tensioner in order to apply tension to the core. Applying tension to the core causes imperfections in the machining to cause pins to bind. The picker then uses a lock pick to find the binding pick and push it until the sheer line between the two pins crosses the line of the core. The picker then proceeds to push all of the pins in place until there are no more pins preventing the rotation of the core.
Disc Detainer
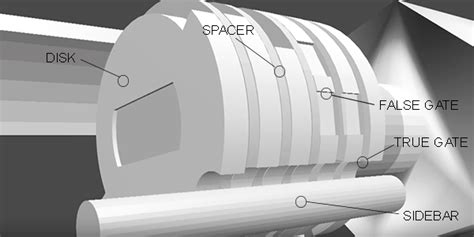
The Disc Detainer lock is a more advanced lock that I have not seen represented in media, and is not nearly as common as a pin and tumbler lock. It is not only a trickier type of lock to pick, but it’s obscurity in relation to the pin tumbler lock means that large numbers of ne’ar-do-wells are not going to be equipped or trained to handle them without resorting to destructive measures. The guts of a disc detainer lock are different from a pin and tumbler lock and as one can guess utilizes a series of discs to keep the core binding. A small(ish) bar is used to keep the core from fully moving as long as it is not recessed within the grooves cut into the discs. One needs to align all of the ‘gates’ in order to get the bar to fall into place and as a result allow the core to turn. The process is incredibly similar to that of the pin and tumbler lock in a general sense, but it uses a single tool designed to manipulate the discs. The picker takes their disc detainer pick and tensions it off of (normally) the first gate. They then move the tongue of the pick through the interior of the core looking for binding discs. Then one by one the picker pushes them into position until eventually the core is free to turn. Just a note on disc detainer picks. With cheaper picks I have found one needs to do modifications in order to allow for them to really function effectively on anything beyond the cheapest of locks. This is usually by decreasing the profile of the tongue to work with narrower discs and modifying the tensioning portion to fit better and actually tension off the locks.
Wafer Locks
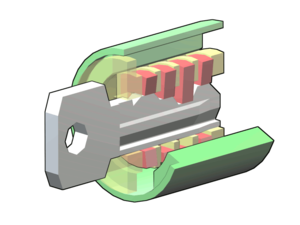
The wafer lock is similar to a pin in tumbler and is also quite common. If one looks at their filing cabinet lock, their $10 document safe, or little lock on a disc and see a rectangular opening, then you have likely found yourself a wafer lock. These are quite quick and easy to pick, with the major difference being that one uses different picks, typically with much less effort to pick compared to a pin and tumbler lock.
Other Lockpicking Methods
There are plenty of other methods than the single pin picking (SPP) described above. I simply went with that since it is one of the more reliable and best ways to handle every lock of a given type regardless of the security measures taken. Skill dictates the capability of SPP for a given lock as opposed to many of the other methods described in this section.
- Raking: Probably the most effective technique for most locks I have encountered. There are mountains of different rakes for different locks, and the methodology is incredibly simple. One applies tension to the lock like normal, then takes the rake and starts aggressively jamming the rake in and out at different angles until luck prevails and the pins all end up in place allowing the lock to spring open.
- Rocking: Rocking is a fantastic method as well, and I also use that quite a bit (really depends if the bogota or the city rake is the most accessible rake). It is similar in the randomness and the fact that is is playing a numbers game like raking, but it is done somewhat differently. One will notice looking at a city rake versus a bogota rake that the city rake is similar to a key bitting and that is what is being used. One goes in and out rocking the pick up and down until luck springs into action and the lock is picked.
- Bump Keys: Bump keys are a very good low skill way of forcing a lock with minimal cosmetic damage. The attacker exploits the same principal that allows the Newtons Cradle to work. The bump key is made by shaving down a key to a specific way to let all the pins rest on the key without shoving them up too far. The attacker then strikes the key with (normally) a type of rubber hammer that causes the key to jam forward the additional distance and bump all the pins. The force transfers from the key pins into the driver pins and while the key pins all stay in place the driver pins are launched up past the sheer line allowing the attacker a window to open the door.
There are plenty of more different types of ways to pick a lock but those three are the ones you are likely to encounter. One can learn an almost endless number of ways to pick an almost endless number of lock types, and so one can get very deep in the weeds if one so desires.
Prevention
So how does one stop one of these many attacks from happening? That is a very big question but I’ll go over some methods I know to weed out all but the most determined attacker. The first thing one can do is to utilize security pins (in a pin and tumbler lock, false gates and security discs I suppose is what one would call the equivalent for disc detainers). These specially designed pins are designed to fall provide false positives for the picker or cause the lock to fall into a false set causing it to turn so much the picker needs to let up on the pressure (and hopefully) causing the set driver pins to fall out. There are several types of security pins such as: Spool Pins, which have a hollowed groove part way down the length causing the core to turn when it hits the pin. Serrated Pins, which have notches all along them causing them to bind hard and making it very hard for the picker to know when they are done and if they have the right pin. There are plenty more but that should give a good idea of the methods of using a security pin. The defender can also utilize a very intimidating keyway. If the attacker can not actually get a purchase inside of the lock then they can not actually pick it. This is achieved by making the keyway contain several extreme angled curves at points the picker would normally insert the pick, or by putting turns in positions that eliminate the picker the ability to get any leverage with their pick by hitting the keyway.
Key Fabrication
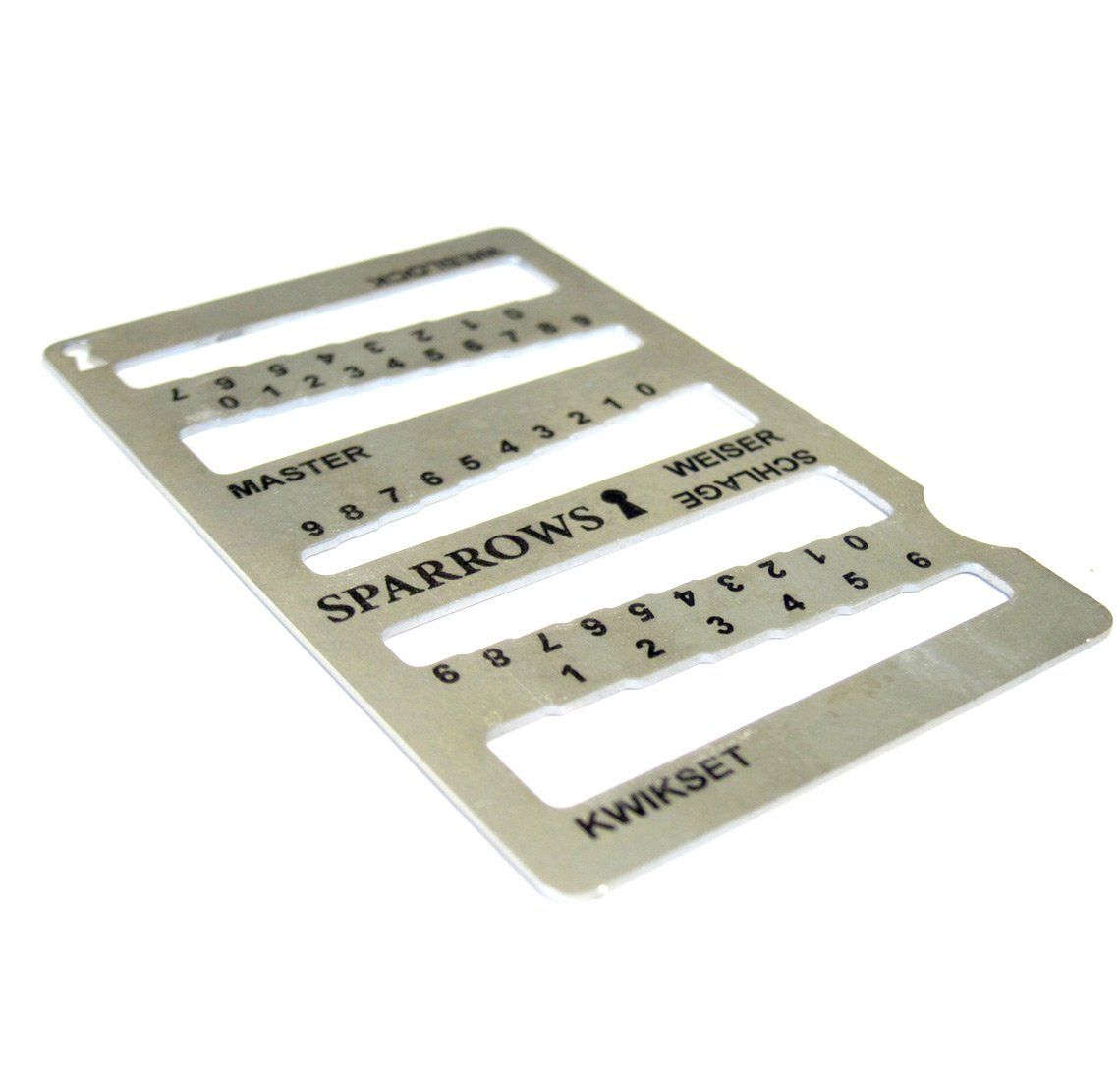
Now if the attacker doesn’t want to/doesn’t know how to pick a lock there are other ways to get in without having your key. One method would be to make a copy of your key, which we will discuss here. First we will talk about general techniques to decode the pattern on someones key with minimal/no interaction with the key itself, and also the ways in which they could make a copy of your key without going to a place that makes copies of keys and might get suspicious when given a series of numbers only. I’ll also go over briefly decoding a master keyed system based on the work of Matt Blaze who is referenced below and gives a significantly better description keyed systems than I could ever give!
Decoding the Key
Decoding a key requires two things. 1) The type of key i.e. Schlage, and 2 the bitting of the key (the depths of cuts in the key). The most sure fire way to get this is to get ones hands on the key itself, and then seeing if it has a small sequence at the top of the key. That number sequence is the bitting of the key and with that one can make a key identical to the key itself. Assuming the key does not have this one can move on to use a decoder (the image above). These have cut outs with a progressively narrower mouth, with little numbers underneath. The attacker can use the decoder to list out the cut of each part of the key and then proceed to fabricate a copy. Lastly, a competent attacker may not even need to have physical access to your key. By taking a picture of the key the attacker can then by knowing the distance for the gets and having a consistent reference (there are a few on a key) the attacker can then decode the key using an overlay after modifying the image slightly to get things lined up. Lastly one can make an impression of the key. There are several clays that do this, and one can use a very wide range of mediums to get the pattern of the key, from using a pencil to trace it, to pressing into a key molding tool, or holding it over a lighter to gather carbon and press it into something. With that they can try to cut out a copy in another material, or fill the mold with a material to get a copy of the key.
Making the Key
There are several ways to get the key made and it depends on the way they have gotten an “image” of the key. If the attacker simply has a trace of the key then they can cut out a version on a stiffer material and then decode that, or if they can cut it out on a thick enough material then they may be able to simply use that material for the key. The attacker may have a mold, and if they do then they could go ahead and pour in the liquid base and let it set. If the imprint is a good one then the key will be very usable, albeit brittle in most cases. Lastly and most effectively in my opinion, is by filing down the keys by hand. With the use of a decoder and the bitting sequence of the target key the attacker can file down the key into the right shape. Since it is not cut mechanically a keen observer may notice the difference in these cuts but the likelihood of this is fairly low.
Rights Elevation
I am not going to even bother trying to do justice to the piece describing how to elevate permissions with access to any key in a master keyed system. Click here to read the article from Matt Blaze.
Prevention
There is really only one thing to do to prevent this and it is keep important keys secure. If anyone can access the key then anyone can copy the key. The same goes for visibility, using key shrouds can prevent an attacker from using images of the key in order to decode the key. Lastly with mastered systems the only real way to prevent elevation is having multiple master keyed systems. Then the attacker would at least need to get access to the higher level keys in order to copy them instead of just needing any key. This can not stop an insider elevating themselves within their own section of the system, but it will at least isolate them.
Loiding

Loiding?
Before talking about Loiding, a recommendation since we are a good way through. If you want some really great videos that relate to physical penetration, and from someone who is actually qualified to talk about these types of topics, check out Deviant Ollam, who has done countless talks about these topics and does an amazing job of describing these things.
Loiding is the process one typically (at least where I am from) learns first in terms of skills to open a door. I don’t know many people in my area who didn’t know how to slip a latch by using a credit card or other flat firm object. While this is a pretty old method and there are countermeasures to this a lot of doors are still existing with exposed latches. The tool shown above is a tool called a travelers hook, which allows the attacker to, well, hook the latch and pull it towards themselves opening the door. This is a really great starting point when attacking a door, if the latch is exposed try and shove it, if you can get it to move then open the door that way without having to do anything damaging, time consuming or requiring skills.
Prevention
There are really only two ways I know to properly handle issues that Loiding, the first and fairly commonly done practice is using a strike plate. A strike plate limits the ability of the attacker to access the latch itself. This is a deterent to really basic loiding approaches like a credit card, but it does not prevent all angles, for example wire, longer hooks, etc. The best way to prevent loiding attacks is through the deadlatch being properly engaged and the door fitting being done properly. The deadlatch prevents the latch from being manipulated when it is engaged and if your door is fitted properly it should be extended fully.
Drilling

This will be a fairly short sub section. The most aggressive way to go about getting through a lock is just to bust it. If you can destroy the locks capability to do it’s job then you can simply open the door. Drilling can be very extreme and annihilate the core (with a large enough drill bit), but what you will normally see is someone drilling right where the pins are located in order to decimate those. This allows the core to turn as the pins that normally prevent the motion of the core are gone. In some more extreme cases you may need to use a larger drill bit to annihilate the entire locking mechanism, this might be if there are special fallback measures in the lock mechanism beyond just the pins preventing the core from moving. Locksmith supply shops contain various different drill bits that you can purchase for these purposes.
Preventing this is usually done by the addition of a hardened plate, hardened pin, or ball bearing. What these do is take advantage of failings of a drill to make it ineffective (short of ridiculous measures or incredibly powerful drills with incredibly hard drill bits). Anyone who has had to drill through sheet metal knows that different gauges and metals require different drill bits to actually drill through. This applies to the lock, if you insert a hardened stell pin the drill is going to whir against it endlessly never getting a bite and being able to tear through it. With a plate you are playing a game of strength against the drill hoping the material of the plate is stronger than the bit being used.
The Hinge

I remember the first exposure I had to a security hinge, and it had absolutely nothing to do with security in the slightest. I worked in a restaurant and we had a huge level of traffic through these swinging double doors that customers entered from. The doors were wooden with glass, in a wooden frame and after 10 years began to drag. I would constantly need to tighten the hinges back into the wall and make sure they were mounted properly, eventually getting to a point where we thought we might need to reframe the door. This was a time sink we really didn’t want to have since that was the only costumer entrance and relying on somone to do it nicely, and quickly was less that likely between operating hours. One customer who was friends with the owners and myself had a suggestion, we could replace the current hinges with security hinges to help them stand up. He being in construction understood better precisely why this would would until the summer when we shut down for a couple of weeks to do remodeling and work around the place. But it worked, the hinge screws no longer needed to be constantly tightened and until the summer when things were redone (the screw holes were in rough condition) the door was working like new.
What I didn’t know at the time was we had significantly upgraded the quality of the door in terms of preventing somone from removing the door. This door really was not security centric and simply separated the front door from the entrance and had no lock or capability to be held shut. But had it been capable of this, and also implemented on all doors we would have made it all but impossible for an attacker to strike the hinges. You see, depending on where the hinges are someone can simply knock the hinge pin out. This is a very low investment attack especially with the right tool, you’ll be able to very simply remove the door from it’s hinges allowing free entry.
What a security hinge does to prevent this is make it so the hinges can not come apart, in one of two ways. First is by securing the hinge pin in place via a screw, the hinge pin is forced in place by a screw that is not accessible when the door is locked, this prevents the hinge from being pulled apart when the door is closed. They can also be secured by riveting the hinge pin caps. This is an improvement on the bottom cap hinge pins one gets for residential doors normally. Unlike your standard bottom cap which can be removed via twist off or a pair of pliers these are actual rivets that can not be removed short of destruction of the caps themselves. The second type of security hinge actually secures the hinge separate from the hinge pin itslef. Small jam pins are embedded where the screw holes are, these are then fit into holes in the hinge that allow them to hold the hinge up on their own. Then if someone removes the hinge pin then those pins will keep the door in place on their own.
Above and Below
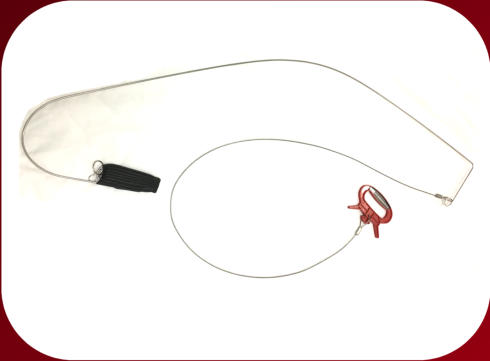
Lastly in the ignoring the lock completely is the methodology of attacking a door by going over or under it. This may be more relevant towards the U.S. and their laws so take this with a grain of salt if it isn’t very applicable to your region. Businesses, hotels, and other public buildings have moved more and more to lever handles as opposed to turn knobs. This is to allow people who are not able to grip the knob firmly to open the doors and exit a building. This is a very good move in terms of increasing access for disabled and elderly patrons, but it does add some security issues. Since the knob is no longer being turned but a lever depressed then it allows for a very specific attack. The attack is fairly simple, using an improvised or special made tool the attacker slides underneath (in some cases over) the door a tool that is designed to go over the latch and allow the attacker to pull it down (or up). These tools can be special made wire and metal contraptions designed to fold down, rolls of film (a la Deviant Ollam), or whatever else does the job. If the attacker can pull on the lever then they are able to get the door opened from the inside. This presents a serious problem of people accessing other peoples hotel rooms or moving around businesses without being stopped by locks.
Preventing this requires a bit of ingenuity on the part of the defender as I do not know any market solution that isn’t a massive shroud making for an incredibly unsightly design. And while for myself unsightly large shrouds are fine, some people can not go for that or afford them. The basic defense is to find a way to prevent the attacker from sliding a thin device around the door handle. This could be something big like a shroud, or a small improvised slot that the handle falls into, preventing anything from slipping around it.
Welp
And that is all I have for now, it took me ages to write this (end of the semester and all that so for extended periods of times I did not do anything), and this ended up being a bit longer than I thought it would be. Obviously everything is obscenely prone to infiltration, and if there is anything I want to get across in this blog, especially the security focused ones, it is that. This isn’t a fear mongery statement but something one needs to consider if one has anything beyond the smallest of threat models. Just because one has a very robust door that won’t be kicked down, or has a nice lock it doesn’t mean that someone with some ingenuity can not bypass it. One should take some time to look at these physical components, because even if you have the most robust firewalls, and the best trained cyber security staff, and nobody in your business is falling for spear phishing campaigns, if I can just open every door and steal all of your drives then not a lot has been accomplished by the robust cyber defenses (I thank Jayson Street for that line of thinking).
Actual References?!?!
(1) Junge, M. B. (1994). The perception of doors: A sociodynamic investigation of doors in 20th century painting. The Arts in Psychotherapy, 21(5), 343–357. https://doi.org/10.1016/0197-4556(94)90062-0
(2) M. Blaze, “Rights amplification in master-keyed mechanical locks,” in IEEE Security & Privacy, vol. 1, no. 2, pp. 24-32, March-April 2003, doi: 10.1109/MSECP.2003.1193208.
